Debian 13 (Trixie) still ships with initramfs-tools by default—a traditional initrd system that gets your system ready to boot. But times are changing. With systemd becoming the standard, the boot process is changing: GRUB is slowly being replaced by systemd-boot, and more and more systems are switching from initramfs-tools to dracut.
So, what makes Dracut special? Unlike traditional initrd systems, Dracut provides a systemd-based early boot environment. This makes it easier to handle complex setups like networking or disk encryption right from the start.
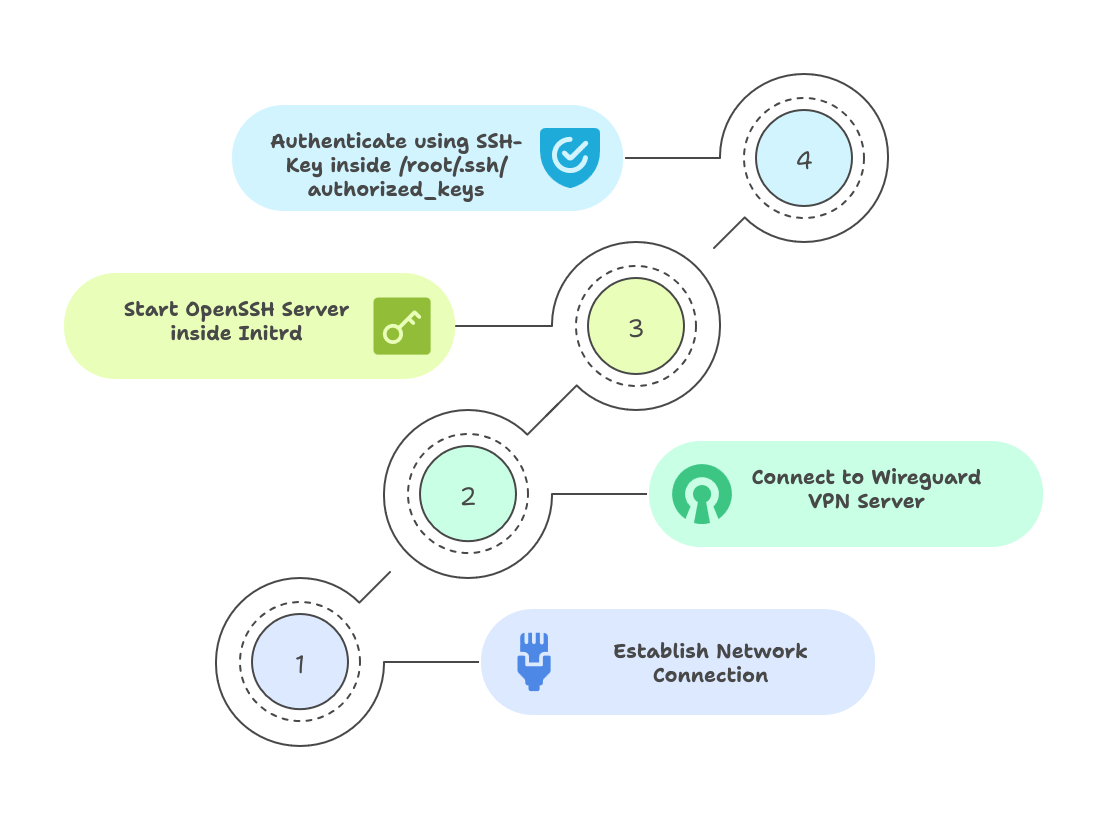
In this post, I’ll walk you through my setup for getting WireGuard VPN working inside Dracut’s initramfs. The idea is simple: you’ll be able to unlock your system remotely over a secure VPN connection during boot. This is a game-changer for headless servers, remote machines, or just anyone who wants a bit more flexibility and security when their system starts up.
This tutorial was tested with Debian 13 (trixie), dracut(108-3) and systemd-boot(257.8).
1. Install the Latest Dracut Version
First, enable the Debian Unstable repositories. If you haven’t done so yet, follow this guide.
Once the repositorie is enabled, install Dracut along with the network module:
sudo apt-get install -t unstable dracut dracut-network
2. Install Required Packages for Initramfs
We need a few essential packages to enable networking and remote access during early boot. These packages will be included in the initramfs:
$ sudo apt-get install wireguard systemd-resolved openssh-server
3. Add the Dracut OpenSSH Module
To enable SSH during early boot, we need the Dracut SSH module. Download and install it:
$ wget https://github.com/gsauthof/dracut-sshd/archive/refs/heads/master.zip
$ sudo unzip -j master.zip "dracut-sshd-master/46sshd/**" -d /usr/lib/dracut/modules.d/46sshd
This will place the module in the proper directory so Dracut can include it in the initramfs.
4. Configure Dracut for Wireguard
Now, create a configuration file for Dracut to include the necessary drivers, modules, and items:
/etc/dracut.conf.d/10-wireguard.conf
add_drivers+=" wireguard "
omit_dracutmodules+=" network-manager "
add_dracutmodules+=" systemd-networkd sshd systemd-resolved "
#add_dracutmodules+=" systemd-networkd sshd "
install_items+=" /usr/bin/wg /usr/bin/ping /etc/systemd/network/99-wg_internal.network /etc/systemd/network/99-wg_internal.netdev "
kernel_cmdline+=" rd.KEYMAP=de "
5. Create Wireguard Network Configuration Files
/etc/systemd/network/99-wg_internal.netdev
[NetDev]
Name=wg_internal
Kind=wireguard
Description=Internal WireGuard tunnel between all devices
[WireGuard]
PrivateKey=<PLACE YOUR PRIVATE KEY HERE>
[WireGuardPeer]
PublicKey=<PLACE YOUR PUBLIC KEY HERE>
AllowedIPs=172.16.255.1/32,fd77:7777:7777::1/128
Endpoint=<VPN ENDPOINT>
PersistentKeepalive=25
/etc/systemd/network/99-wg_internal.network
[Match]
Name=wg_internal
[Network]
Address=172.16.255.20/24
Address=fd77:7777:7777::20/64
6. Regenerate Initramfs
After configuring Dracut, regenerate the initramfs so your changes take effect:
$ update-initramfs -u -k all
Now, your system is ready to boot with WireGuard and SSH enabled in the initramfs, allowing remote unlocking and secure access even before the main system starts.